Single Sign-On & OKTA
This article will help Administrators set up SSO with the help of OKTA
What is Single Sign-On?
Single Sign-On is an authentication system that enables users to securely log in to multiple independent software systems by logging in only once into a managed authentication system. This means your users need to remember only one user ID and password but without any risk to your security.
The managed authentication system is called Identity Provider (or IdP, for example, G-Suite, Okta) and the applications that rely on this Identity Provider are called Service Providers
Setting up SSO for your Outplay account ensures that your employees can log in to Outplay using an identity provider of your choice, such as G-Suite, and not have to create another login ID and password separately.
What is SAML? How does SAML work?
SAML is a very widely used XML-based authentication framework to securely exchange information between an Identity Provider (like Okta) and Service Provider (like Outplay). As part of this setup,
The Service Provider trusts the Identity Provider (IdP) to verify the user’s authentication
The Identity Provider, on successful authentication, exchanges the user’s identity via a digitally signed authentication assertion with the Service Provider (SP) enabling a seamless login for the user.
In short, SAML is a standard security protocol that enables IdPs to securely let SPs like Outplay know whether you are you.
Here is a list of some common terminologies you may encounter when trying to set up SAML SSO for Outplay:
Service Provider (SP) Entity ID: This is the entity providing the service or web application. In our case, the SP is Outplay.
Identity Provider type (IdP): This is the entity that is capable of authenticating the user’s identity. Popular IdPs are Azure AD, G-Suite, Okta, and OneLogin.
SAML Request: Also known as the authentication request. When a user tries to log in using SSO, the service provider generates this request to the identity provider.
SAML Response: The identity provider is responsible for generating the SAML response in XML format which contains the details of the user whose authentication is validated by the IdP. SAML Response is constructed by the IdP based on the mutually pre-configured information for a given SP. Once an SP receives the SAML response, it is the SP's responsibility to validate the response generated by the appropriate IdP and then parse the user's identity information embedded in the SAML response.
ACS URL: This is the public endpoint from the SP side that IdP will post the SAML Response to.
SAML SSO URL or Login URL: This is the public endpoint from the IdP side that the SP will send the SAML Request to.
Prerequisites - As Outplay provides SSO through OKTA, we would need to create an application within Okta as Outplay and then add the details required as per the steps mentioned below.
The users need to have Okta tenants with admin rights.
The user needs to have an Outplay Account with admin rights.
Adding Outplay to Okta
For the applications to communicate with each other, we would need to follow the below-mentioned steps.
Log in to your Okta admin account
Go to Applications.
Click on “create App Integration”.
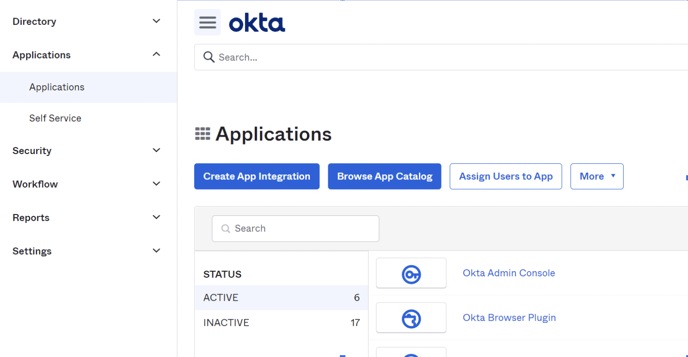
Choose “SAML 2.0” & click Next.

Add the Outplay logo and name as shown below -

[](https://outplay.intercom-attachments-7.com/i/o/416126412/3c25b2209eef027641a814e4/FJ6tffJdjOQeMT2mtjaEWHYZuFhFyUajvl6Lc2rsRh1PjZz60KhYMyMbsin21rFhlciBfpSmcReovnHujhDplX36Tjt09TdCcfUL_em-pGNIAcRjubN88Cpq9SFlsM7lDb4FRUmz)
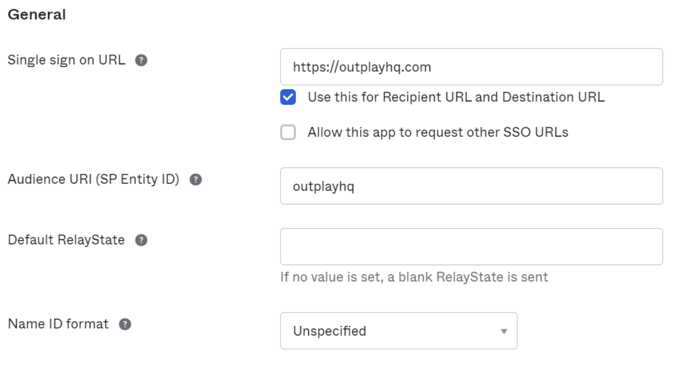
Add the “**Single Sign-On URL**” as “[https://outplayhq.com](https://outplayhq.com/)”.
Add the Audience URL ( SP Entity ID ) value as _outplayhq_, and click next, we will come back to this section after configuring other settings.
In the next section, choose “**I’m an Okta customer adding an internal app**” & “**This is an internal app we have created**”, and select the toggle, click finish as per the screenshot,

Now the application will be created and you will be redirected to the application page. Click on the “**Sign On**“ tab. Under the “**View Setup Instructions**“ button, you will see the “I**dentity Provider metadata**“ link. Copy this link’s address.

This is your metadata URL, we will use this URL to configure Okta inside Outplay.
Now log in to your Outplay account. Navigate to the “**Settings**” --> “**Org Settings**” page and click on the “**Single Sign-on**” tab.

Click on “**Add Identity Provider**“. Fill in the provider name. Choose the “**Provider Type**“ as “**Okta**“ and fill the “**Metadata URL**” value with the URL that you copied before, screenshot is attached below.
After clicking on “Save”, the identity provider will be added to your identity provider list. Click on the identity provider row to see its details. It will open a popup window such as shown below.
Now navigate back to the Okta application screen.
Under the “General“ tab click on “Edit“ on the “SAML Settings“ section. Copy the value of “**Assertion Consumer Service (ACS) URL**“ from the identity provider details popup in Outplay and paste it in the “**Single sign-on URL**“ field in Okta.
Similarly, copy the value of “**Service Provider Entity ID / Audience URL**“ from the identity provider details popup in Outplay and paste it in the “**Audience URI (SP Entity ID)**“ filed in Okta.
Save the settings within Okta.
Now navigate back to Outplay, and you will see the identity provider prompt.
Click on the “Enable“ toggle box of the newly added identity provider. It will ask for a confirmation, click on “Enable“ to proceed.
Note:- You can add multiple identity providers to your account but at any moment only one provider can be enabled for Single Sign-on functionality.
User Assignment
Once Okta has been configured with Outplay. You would need to assign users to this application in Okta to let them use SSO with Outplay.
Steps as below -
Log in to your Okta admin account
Go to Applications and click on Outplay.
Under the assignment tab, click on “Assign”.
“Assign to People“ (or you can select the “Assign to Groups“ option if you have user groups) and choose the users that you want to assign to this application for login.
Once you choose a person, you will be asked for the “User Name“ value, put the corresponding user’s Outplay login email address in this field, and save. Now the assigned users will be able to log in to Outplay through Okta.
SSO Deactivation
To deactivate Okta SSO login in Outplay.
Go to “Settings“-->“Org Settings“--> “Single Sign-on“.
Disable the identity provider from the list (additionally, you can deactivate the Outplay app in Okta as well).
Once the SSO is disabled, users will no longer be able to log in via Okta.
They need to reset their password in the Outplay login screen and then they will be able to log in with their new password.
Updated on: 18/03/2025
Thank you!