Introduction
System and user logs play a pivotal role in tracking and recording various activities within a platform. These logs are a valuable resource for administrators and users alike, offering insights into changes, modifications, and key actions performed within the system. In this knowledge-based article, we'll delve into the specifics of system/user logs, focusing on the comprehensive tracking of user activities, including settings modifications, user/role/permission changes, and more.
I. What Are System/User Logs?
System and user logs are records that capture and document the activities and events occurring within a system. These logs serve as a historical record, enabling administrators to review, analyze, and troubleshoot issues, as well as maintain security and compliance.
II. Importance of Activity Tracking
Activity tracking within logs is crucial for several reasons:
-
Security: Logs provide a trail of user actions, helping to identify suspicious activities and potential security breaches.
-
Auditability: System logs support compliance requirements by documenting changes made to settings, users, roles, and permissions.
-
Troubleshooting: When issues arise, logs serve as a valuable tool for diagnosing problems, understanding the sequence of events, and implementing effective solutions.
-
Accountability: Tracking user activities promotes accountability, ensuring that actions within the system can be attributed to specific users.
III. Types of Activities Recorded
a. Settings Enabled/Disabled
The logs capture changes made to system settings, including the enabling or disabling of specific features or configurations. This is particularly useful for understanding how system functionality evolves.
b. User, Role, and Permission Changes
Logs document any modifications to user accounts, role assignments, and changes in permissions. This feature is essential for managing user access and ensuring that roles and permissions align with organizational needs.
c. Login and Logout Events
User login and logout events are logged, providing a timeline of user sessions. This information aids in monitoring user activity patterns and detecting unauthorized access.
d. Data and Content Changes
Logs also track changes made to data and content within the system. This includes additions, deletions, and modifications to records or files, offering a comprehensive view of content-related activities.
IV. Accessing System/User Logs
Access to logs is typically restricted to administrators or users with specific permissions.
Users with permissions can access system logs by navigating to the Engagement tab and clicking on settings, under settings, you will be able to view a page called System Logs.
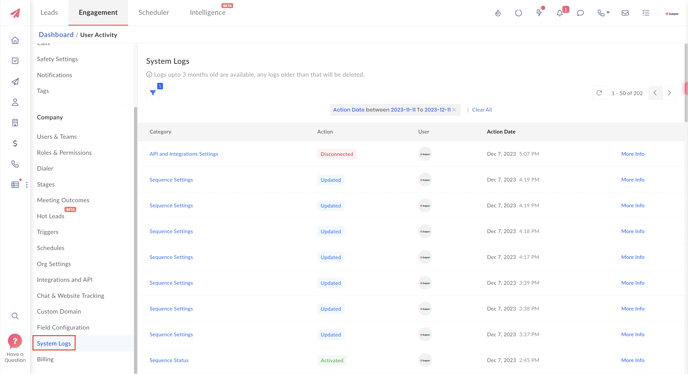
V. Best Practices for Utilizing System/User Logs
- Regularly review logs to stay informed about system activities.
- Set up alerts for critical events to enable real-time response to potential issues.
- Establish a log retention policy to balance storage needs with compliance requirements.
- Train users and administrators on interpreting and leveraging log data effectively.
VI. Conclusion
Understanding and leveraging system/user logs is essential for maintaining the integrity, security, and efficiency of a platform. By harnessing the power of detailed activity tracking, users and administrators can make informed decisions, troubleshoot effectively, and ensure that their systems operate seamlessly and securely.